LinkDaddy Universal Cloud Storage: Safeguard and Reputable Solutions
LinkDaddy Universal Cloud Storage: Safeguard and Reputable Solutions
Blog Article
Secure Your Information Anywhere With Universal Cloud Storage
In an age where data safety is paramount, services and individuals seek dependable options to safeguard their information. Universal Cloud Storage presents an engaging alternative for those looking to firmly save and access data from any type of location. With its advanced security methods and flexible accessibility functions, this solution guarantees that information continues to be readily available and protected whenever needed.
Benefits of Universal Cloud Storage Space
Universal Cloud Storage space offers a myriad of benefits, making it an essential device for securing and accessing information from different locations. One of the essential benefits of Universal Cloud Storage space is its adaptability. Individuals can access their information from anywhere with an internet connection, making it possible for smooth partnership among staff member despite their physical place. This accessibility also ensures that information is always available, decreasing the threat of losing vital details due to equipment failures or crashes.

Information Security and Safety And Security Steps
With the raising reliance on cloud storage for information ease of access and collaboration, guaranteeing robust information file encryption and safety procedures is important in safeguarding sensitive information. Information file encryption plays a crucial duty in securing data both in transit and at remainder. By encrypting information, info is converted right into a code that can only be deciphered with the appropriate decryption key, adding an additional layer of security versus unapproved access.
Carrying out solid authentication approaches, such as multi-factor verification, aids verify the identity of individuals and protect against unapproved individuals from acquiring access to delicate information. On a regular basis updating safety and security methods and patches is necessary to resolve potential vulnerabilities and make sure that safety and security procedures remain reliable against evolving hazards.
Furthermore, making use of end-to-end security can supply an additional degree of security by making sure that information is secured from the point of origin to its final location. By adopting an extensive strategy to data encryption and safety and security measures, organizations can improve data defense and mitigate the risk of information breaches or unauthorized gain access to.
Accessibility and Cross-Platform Compatibility
Ensuring information access and cross-platform compatibility are essential considerations in optimizing cloud storage remedies for seamless user experience and efficient collaboration. Cloud storage solutions need to give users with the capacity to access their information from numerous devices and running systems, making sure performance special info regardless of location or innovation preference.
By offering cross-platform compatibility, customers can flawlessly switch over in between devices such as desktop computers, laptop computers, tablet computers, and mobile phones with no obstacles. This adaptability enhances customer ease and productivity by allowing them to deal with their information from any type of gadget they prefer, advertising partnership and effectiveness.
Moreover, ease of access attributes such as offline gain access to and synchronization guarantee that users can watch and edit their information even without an internet connection. This capability is crucial for users who often travel or work in locations with bad connectivity, ensuring continuous access to their crucial files.
Backup and Disaster Recovery Solutions
To fortify information integrity and functional continuity, robust backup and disaster recuperation solutions are crucial parts of an extensive cloud storage space framework. Backup services guarantee that data is read review consistently replicated and saved safely, reducing the threat of data loss due to unintentional removal, corruption, or cyber hazards. Calamity recovery solutions, on the various other hand, focus on swiftly recovering procedures in case of a catastrophic occasion like natural catastrophes, system failures, or cyber-attacks.
Reliable back-up strategies involve producing numerous copies of data, keeping them both in your area and in the cloud, and applying automatic back-up processes to make sure uniformity and integrity. Universal Cloud Storage Service. Disaster recuperation strategies consist of predefined treatments for data remediation, system recovery, and functional connection to reduce downtime and reduce the impact of unexpected interruptions
Finest Practices for Information Security
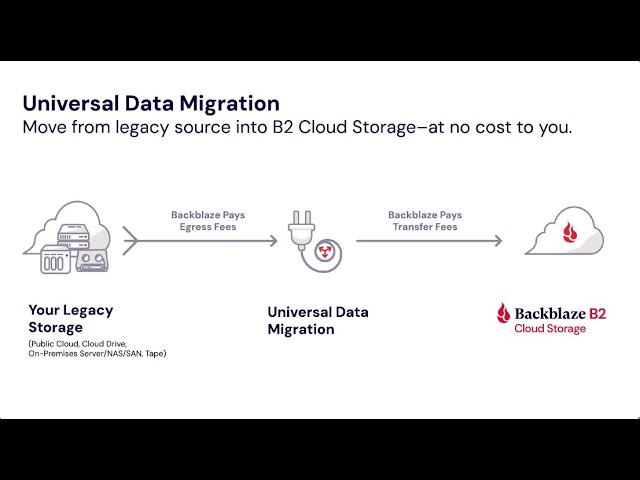
In addition, establishing accessibility controls based on the principle of least benefit aids limit accessibility to delicate information only to those who need it for their duties. Carrying out routine safety audits and assessments can aid recognize weaknesses in information defense procedures and resolve them immediately. In addition, developing and implementing data backup procedures makes certain that data can be recouped in case of a cyber occurrence or information loss. By adhering to these finest practices, organizations can improve their data defense methods and reduce possible threats to their information assets.
Conclusion
Finally, Universal Cloud Storage space uses a reliable and protected option for keeping and accessing data from anywhere with an internet connection. With durable security procedures in place, data is shielded both in transportation and at rest, making certain discretion and stability. The availability and cross-platform compatibility functions make it possible for smooth collaboration and productivity across various devices and operating systems, while back-up and catastrophe recovery solutions supply comfort by protecting versus information loss and making sure swift repair in instance of emergencies.

Report this page